Dfns SSO supports all OpenId Connect (OIDC) providers. You can configure your organization to use SSO and redirect your users automatically to your SSO when they are trying to log into Dfns.
Note that you still need to invite users using the user management page. Users coming from the SSO without being invited to your Dfns organization won’t get access.
Initiate SSO Configuration in Dfns
First, you’ll need to start the SSO configuration process within your Dfns dashboard to obtain the necessary Redirect URI.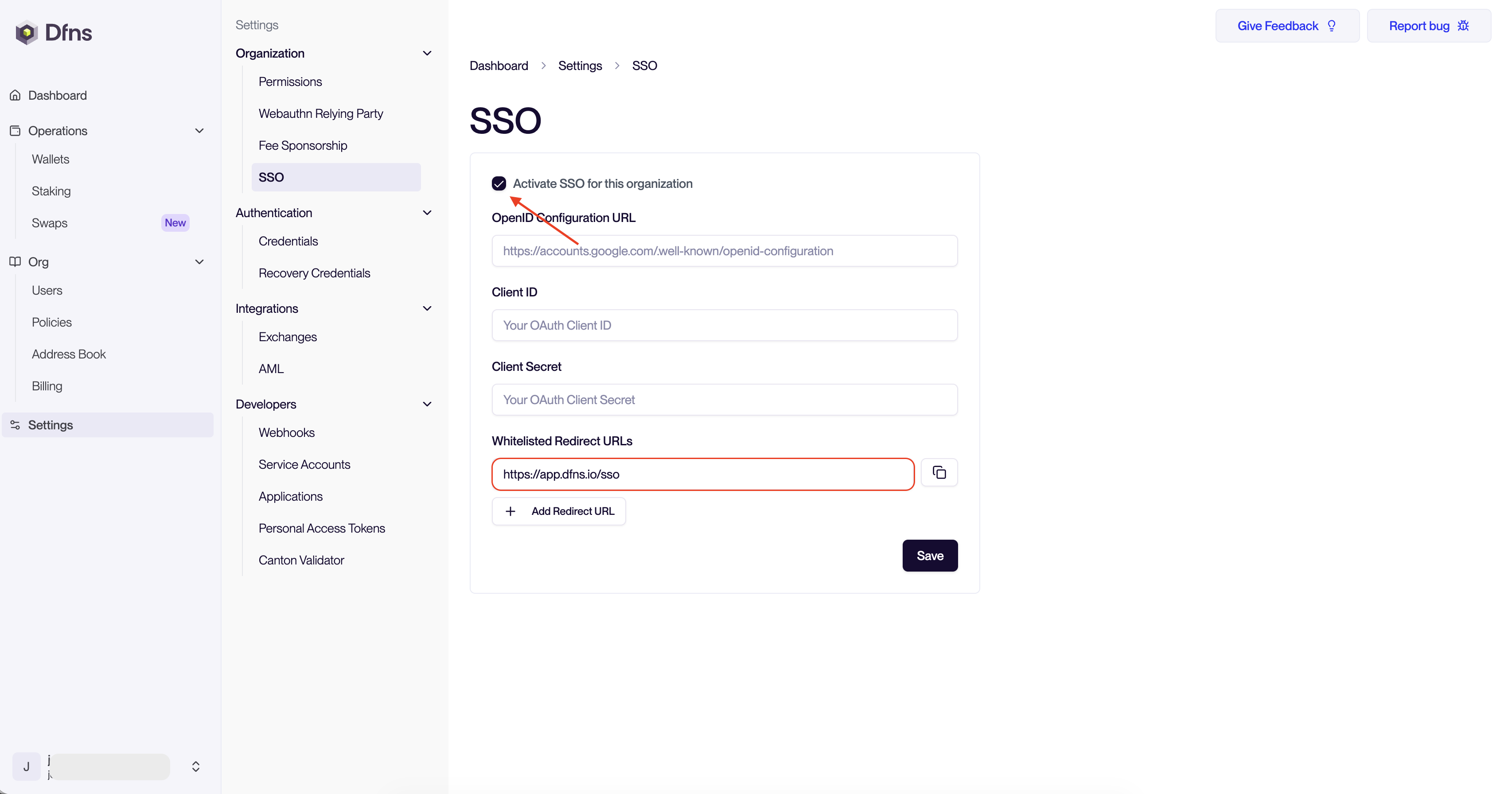
- Log in to your Dfns dashboard and navigate to the Settings > SSO page.
- Check the Activate SSO for this organization checkbox.
- Copy the Redirect URL. You will need this to configure your identity provider. Note that if you are building another frontend for your customer then you can also add their redirect URLs here.

Configure Your Identity Provider
Next, you’ll need to configure an application in your identity provider’s dashboard. Below are instructions for our most common providers.
Okta
Okta
A detailed step-by-step tutorial can be found here.
-
Create a New App Integration:
- Log in to your Okta admin dashboard.
- Navigate to Applications > Applications and click Create App Integration.
- Select OIDC - OpenID Connect as the sign-in method and Web Application as the application type. Click Next.
-
Configure General Settings:
- Give your application a descriptive name, like “Dfns dashboard”.
- In the Sign-in redirect URIs field, paste the Whitelisted Redirect URL you copied from the Dfns dashboard.
- Under Assignments, choose to limit access to specific groups or allow everyone in your organization.
- Click Save.
-
Obtain Client Credentials:
- On the Client Credentials section, you will find the Client ID and Client Secret (under Client Authentication). Copy these values; you’ll need them to finalize the setup in Dfns.
Entra ID (formerly Azure AD)
Entra ID (formerly Azure AD)
A detailed step-by-step tutorial can be found here.
-
Register a New Application:
- Log in to the Microsoft Entra admin center.
- Navigate to Entra ID > Applications > App registrations and click New registration.
- Enter a name for your application, like “Dfns”.
- Under Redirect URI, select Web and paste the Whitelisted Redirect URL from the Dfns dashboard.
- Click Register.
-
Obtain Application (Client) ID:
- From the application’s Overview page, copy the Application (client) ID.
-
Create a Client Secret:
- Navigate to Certificates & secrets, in the Client secrets tab click New client secret.
- Add a description, choose an expiration period, and click Add.
- Copy the Value of the client secret immediately, as it will not be shown again.
-
Obtain the Configuration URL:
- From the application’s Overview page, click the Endpoints tab.
- Copy the OpenID Connect metadata document URL. This is your OpenID Configuration URL.
Google Workspace
Google Workspace
A detailed step-by-step tutorial can be found here.
-
Create a New Project (or use an existing one):
- Log in to the Google Cloud Console.
- Create a new project or select an existing one.
-
Configure OAuth Consent Screen:
- Navigate to APIs & Services > OAuth consent screen.
- Choose Internal as the user type and click Create.
- Fill in the required app information, such as the app name and user support email.
- Add the necessary scopes:
openid,email, andprofile.
-
Create OAuth Client ID:
- Go to APIs & Services > Credentials and click Create Credentials > OAuth client ID.
- Select Web application as the application type.
- Under Authorized redirect URIs, click Add URI and paste the Whitelisted Redirect URL from the Dfns dashboard.
- Click Create.
-
Obtain Client ID and Client Secret:
- A pop-up will appear with your Client ID and Client Secret. Copy these values.
Finalize SSO Configuration in Dfns
Now that you have the required information from your identity provider, return to the Dfns dashboard to complete the setup.
- Go back to the Single Sign-On (SSO) configuration page in Dfns.
- Enter the following information you obtained from your identity provider:
- OpenID Configuration URL: the configuration URL (for Okta and Entra ID) or issuer URL (for other OIDC providers). For example:
- Okta:
https://{tenant-domain}/.well-known/openid-configuration - Google:
https://accounts.google.com/.well-known/openid-configuration - Entra:
https://login.microsoftonline.com/xxxx/v2.0/.well-known/openid-configuration
- Okta:
- Client ID
- Client Secret
- OpenID Configuration URL: the configuration URL (for Okta and Entra ID) or issuer URL (for other OIDC providers). For example:
- Click Save.
Invite users with SSO
Now head to the Users page and Invite a new user. In the form you can check “require SSO” to force the user to go through the SSO to log into Dfns.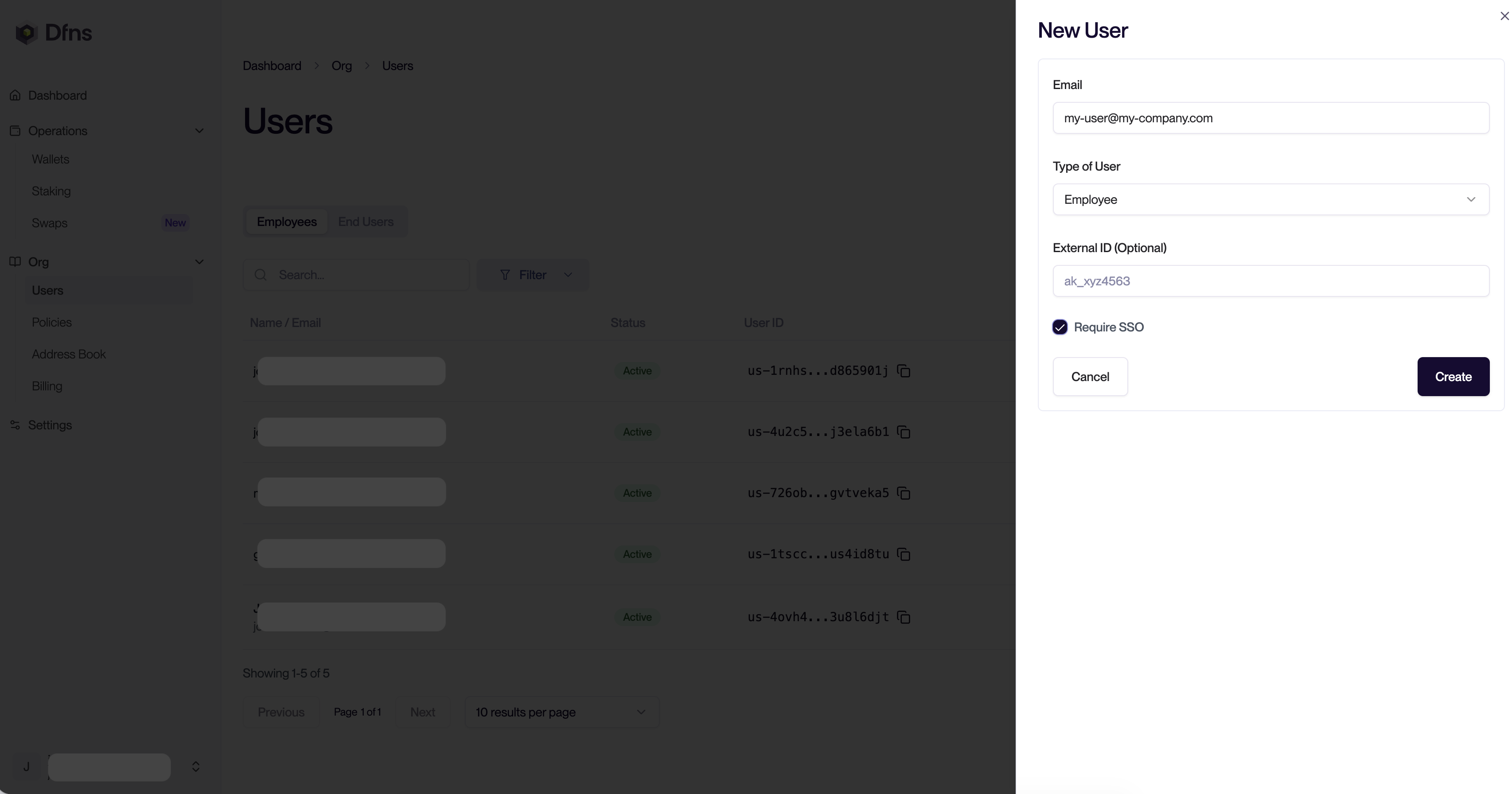

Require SSO for existing users
Now head to the Users page and click the menu behind a user, and enable SSO. Those users will have to go through the SSO in order to log into Dfns.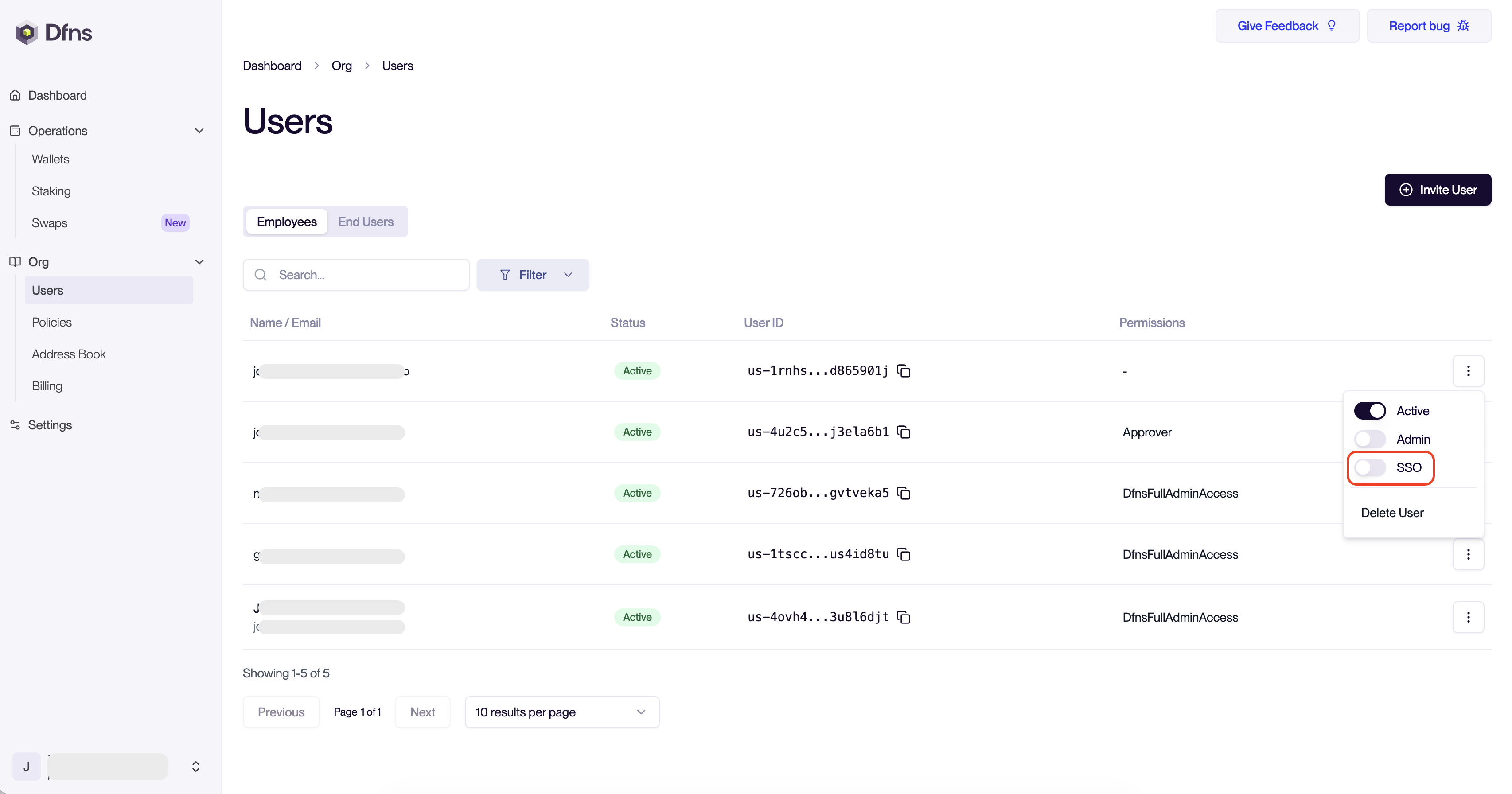
For this step you need the
Auth:Users:Update permission.
Log users in through SSO
Once SSO is set up for a user, they will always be redirected to your identity log in page:
- Default Dfns dashboard login
https://app.dfns.io: users will be required to sign in with their passkey, then be redirected to the SSO page. - Direct URL to your SSO: user will log in and will be redirected to the Dfns dashboard automatically. They won’t need to use their passkey.
- Dfns SSO redirection URL
https://app.dfns.io/sso?orgId=or-*****&clientId=yourSSOclientId: users will be redirected to your SSO automatically, without requiring to use their passkey.
Your SSO integration is now complete! Your team members can now log in to Dfns using their credentials from your identity provider.
