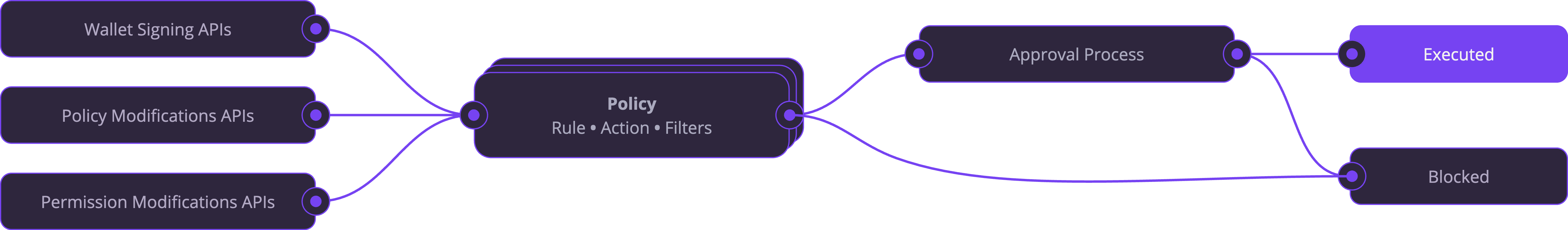
Default behavior: If no policies are configured, all transactions are allowed. Policies add restrictions on top of the default “allow all” behavior - they are not a whitelist.
All policies are evaluated: When an activity occurs, every matching policy is evaluated. Policies cannot bypass or override each other - if any policy triggers a
Block action, the activity is blocked. If multiple policies trigger RequestApproval, approvals from all triggered policies are required before the activity proceeds.- For payments over $100,000, request approval from a Vice President.
- For payments over $250,000, request approval from both a Vice President and a Managing Director.
- Large Payment:
- Rule:
TransactionAmountLimitwith amount value of $100,000. - Approval scoped to VicePresidents.
- Rule:
- Very Large Payment:
- Rule:
TransactionAmountLimitwith amount value of $250,000. - Approval scoped to ManagingDirectors.
- Rule:
Available rules
| Rule | When it triggers |
|---|---|
AlwaysTrigger | Every signature request requires approval (or is blocked) |
TransactionAmountLimit | Transactions above a USD threshold require approval |
TransactionAmountVelocity | Total value transferred from a wallet exceeds a limit within a time window |
TransactionCountVelocity | Number of transactions from a wallet exceeds a limit within a time window |
TransactionRecipientWhitelist | Transactions to addresses not on your approved list |
ChainalysisTransactionPrescreening | Outbound transactions flagged by Chainalysis KYT |
ChainalysisTransactionScreening | Incoming transactions flagged by Chainalysis KYT |
GlobalLedgerTransactionPrescreening | Outbound transactions flagged by Global Ledger KYT |
TravelRuleTransactionPrescreening | Transfers requiring travel rule compliance (via Notabene) |
Approval process
When a policy triggers with theRequestApproval action, the transaction is held until enough approvers sign off. This is configured using approval groups and quorums:
- Approval group: A set of users who can approve. You can specify exact user IDs, or allow anyone in the organization.
- Quorum: The minimum number of approvals needed from that group. For example, “2 out of 5 admins must approve.”
Automating with Service Accounts
When automating transactions with Service Accounts, you may need certain wallets to bypass approval workflows (e.g., automated payouts, scheduled transfers).Using wallet tags
Use wallet tags to scope policies to specific wallets. Tag the wallets that need approval workflows, leaving automated wallets untagged:- Tag wallets that need approval: Add a tag like
requires-approvalto wallets managed by humans - Create policies with filters: Target policies only at tagged wallets
requires-approval. Automated wallets without this tag won’t trigger the policy.
