Fully-managed MPC in Dfns Cloud
This is the standard, default, and most popular option. In this model, Dfns securely manages all the key shares within our robust, geographically distributed cloud infrastructure. It’s a turnkey solution that provides institutional-grade security with zero operational overhead for your team.- You get: Maximum convenience and the full security of the Dfns platform without managing any infrastructure.
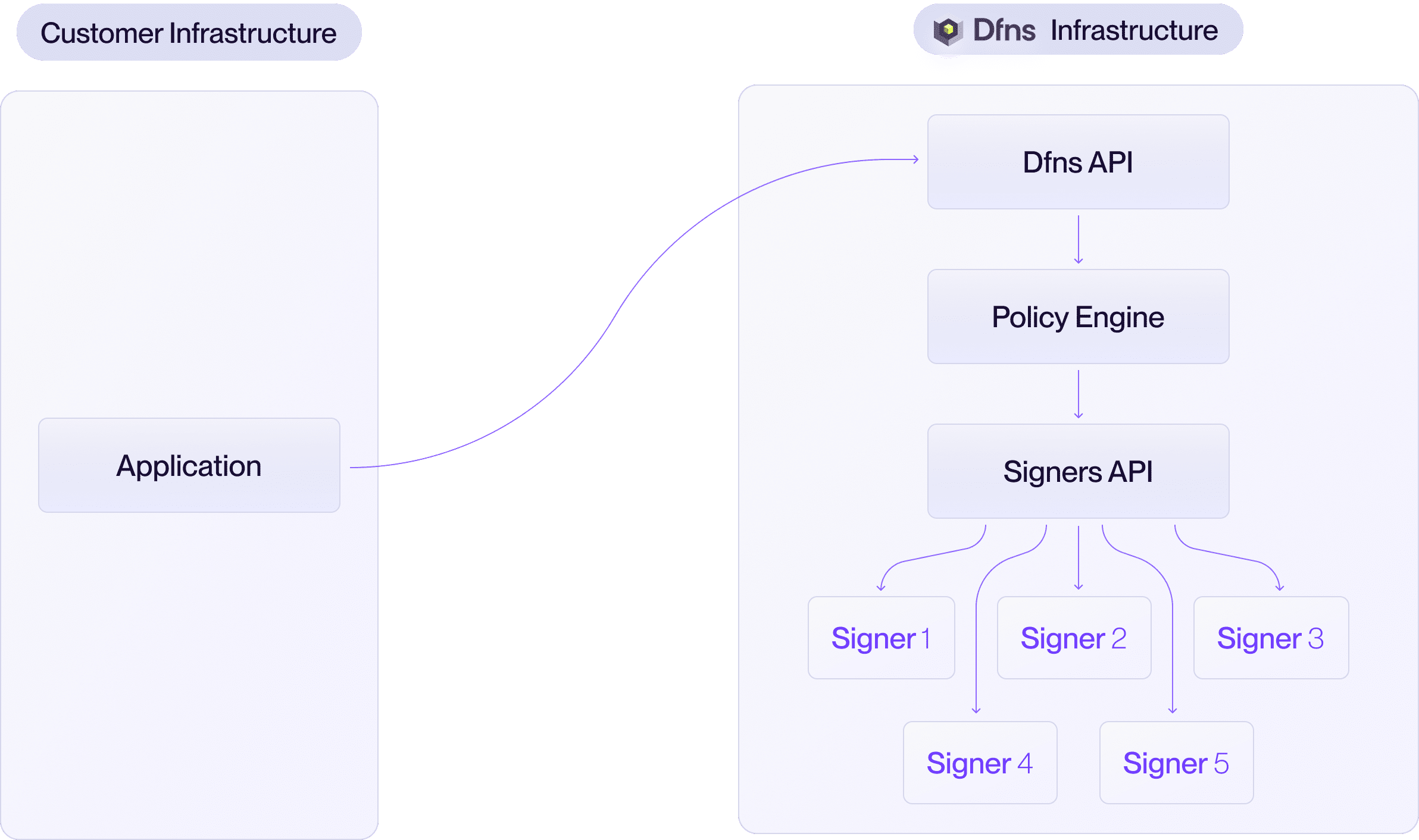
Hybrid MPC
The Hybrid model offers a powerful balance of control and convenience. Dfns manages a portion of the key shares in our cloud, while your organization securely holds one or more shares within your own environment. This makes you a required participant in every signing ceremony, giving you a direct cryptographic veto over any transaction. In this model, you deploy and operate a Signing Server (provided by Dfns) within your infrastructure. This server securely stores your key share(s) and interfaces with Dfns during signing operations.- You get: Shared security responsibility and direct control over transaction finality.
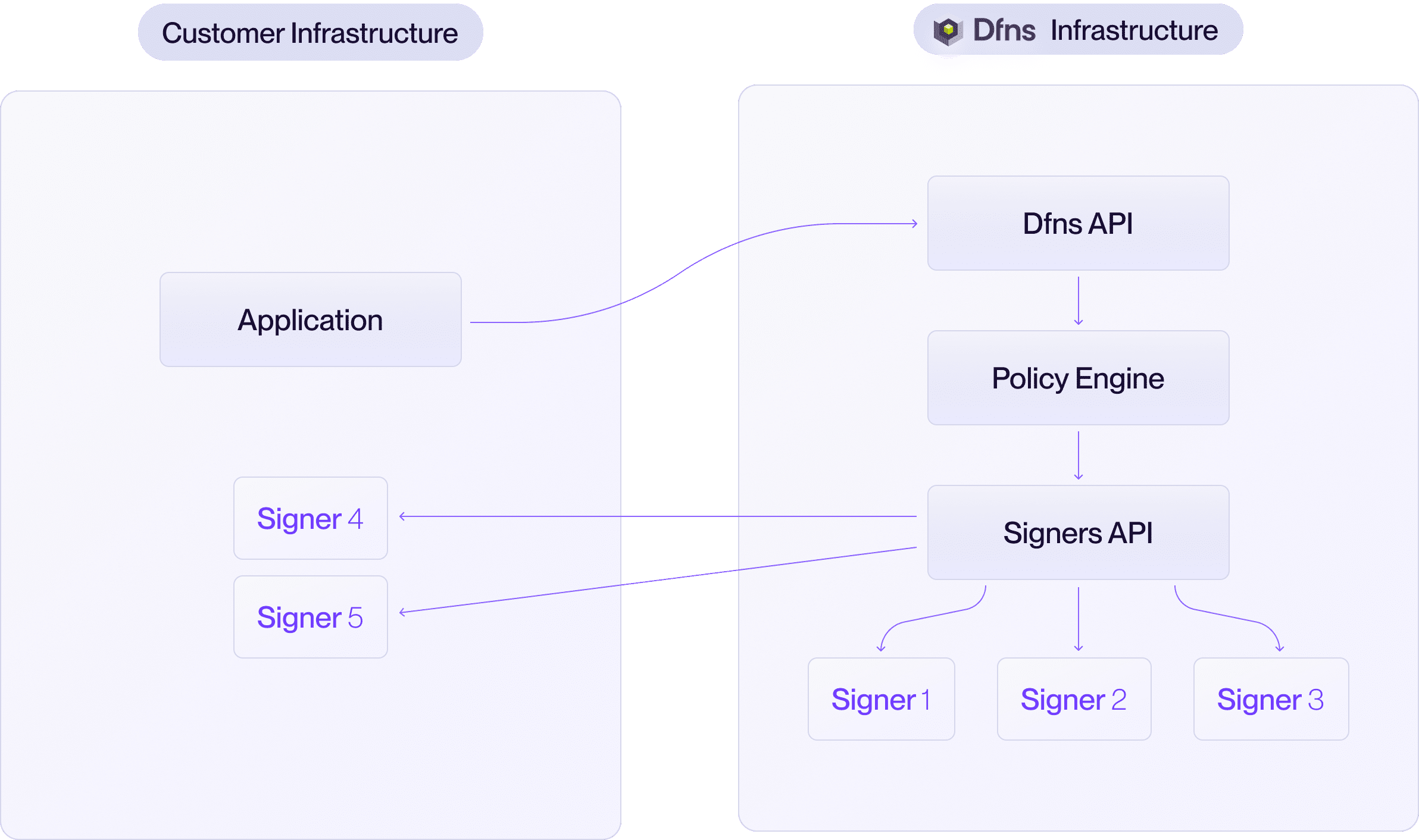
You can choose your preferred MPC threshold scheme (we recommend 3-out-of-5, but any configuration can be implemented) as well as how many signers are operated by Dfns versus your organization.
On-Premise / Self-Hosted MPC
For organizations with the strictest data residency, compliance, or infrastructure requirements, we offer a fully on-premise deployment. In this model, you run the Dfns signing software and manage all key shares entirely within your own data centers or private cloud. In this model, you are responsible for deploying, operating, and maintaining the entire signing infrastructure, including the Signing Server and key shares. Dfns provides the software and support, but all cryptographic operations occur within your controlled environment.- You get: Maximum control over your keys and infrastructure.
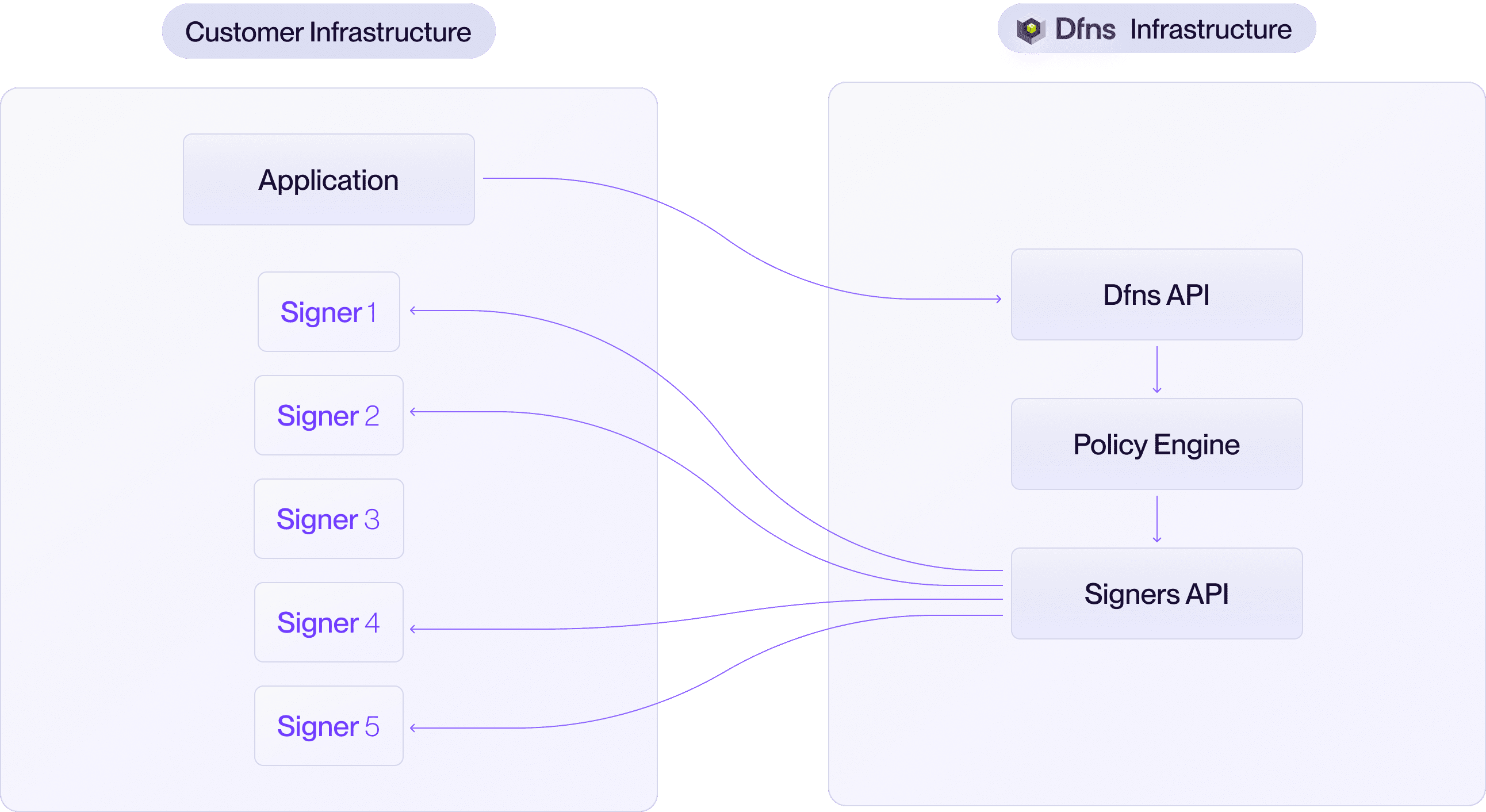
You can choose your preferred MPC threshold scheme. We recommend 3-out-of-5, but any configuration can be implemented to match your security requirements.
On-Premise HSM
For organizations seeking to add a layer of physically-enforced, tamper-resistant security to your cryptographic operations, ensuring your key shares never leave the protected boundary of your hardware, Hardware Security Modules (HSMs) are the gold standard. Dfns supports integrating customer-owned HSMs. In this model, you deploy the HSMs and an HSM Driver that interfaces with your HSM using the PKCS#11 standard. The HSM Driver handles communication between Dfns and the HSM, ensuring that keys are securely managed and signing operations are performed within the HSM’s protected environment.- You get: Key security with hardware-enforced protections and full control over your cryptographic environment.
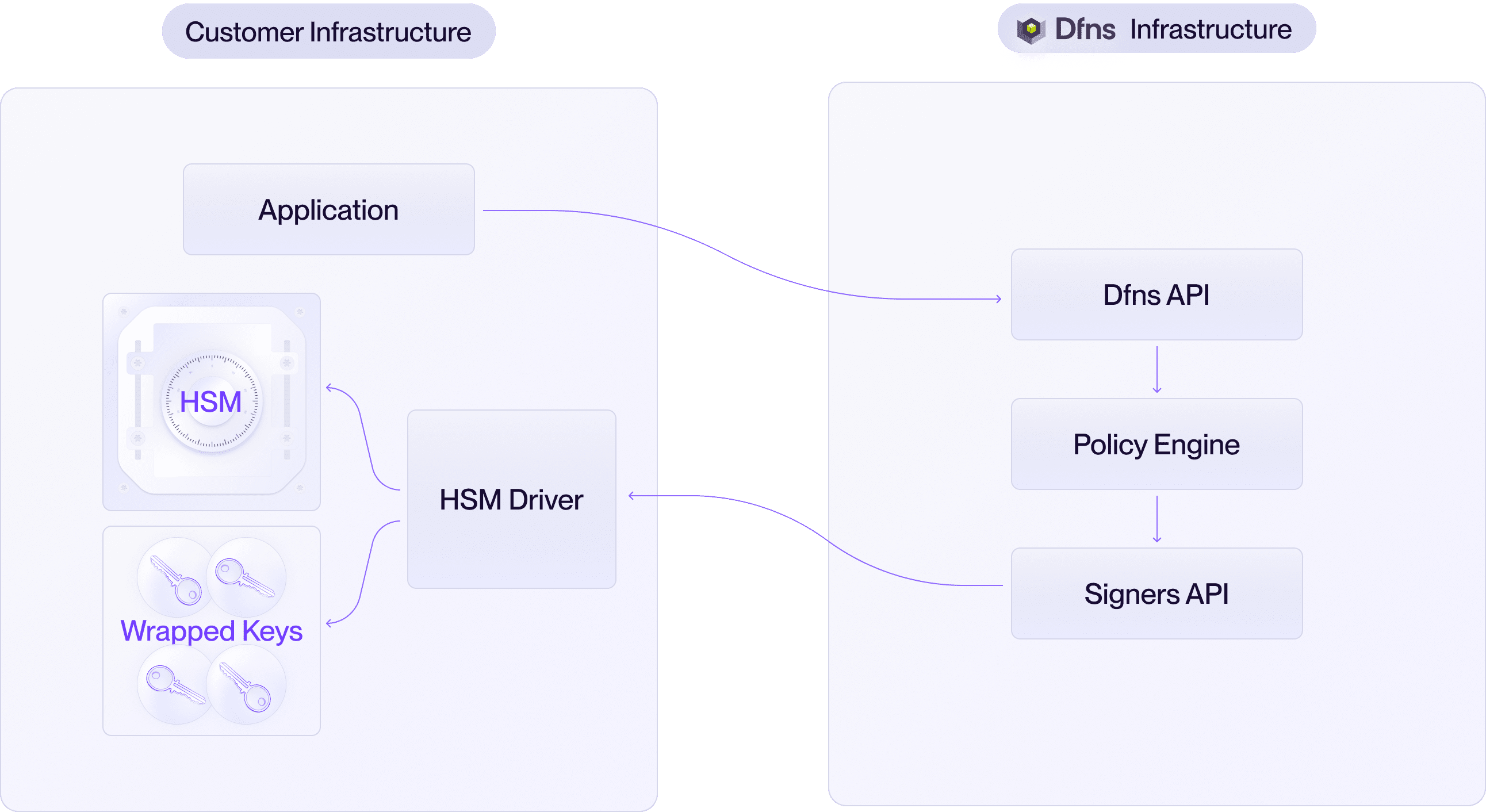
Choosing the Right Model for You
The best model depends on your specific needs for control versus convenience. The table below outlines the key differences to help you decide.| Feature | Dfns Cloud (Fully-Managed) | Hybrid Cloud | On-Premise (Self-Hosted) |
|---|---|---|---|
| Key Share Custody | All shares secured and stored by Dfns | Shared (Dfns & Customer) | All shares held by Customer |
| HSM Support | No | No | Yes |
| Primary Benefit | Simplicity & Speed | Shared Control & Veto Power | Maximum Control & Data Residency |
| Best For | Most startups, fintechs, and enterprises that want to move fast without managing infrastructure. | Institutions that require a cryptographic role in transaction signing for compliance or internal policy. | Financial institutions or government entities with strict data locality rules or dedicated internal security teams. |
